Developer Guide
REST API Overview
The IoTRoutes REST API exposes all core platform functionalities for external systems, integrations, and automation scripts.
Through the API, developers can manage devices, send commands, query the attribute ledger, handle workflows, and interact with stored files.
The API follows RESTful conventions, uses JSON as the data format, and requires JWT-based authentication for every request.
For devices communication over HTTP with the Platform, some APIs , can be accessed also with Client ID and API Key
1. API EndPoints
All platform API endpoints are exposed under the base path https://<your-AOS-url>/<your-subscription>/api/ .
For example on the cloud version https://aos.iotroutes.com/<your-subscription>/api/.
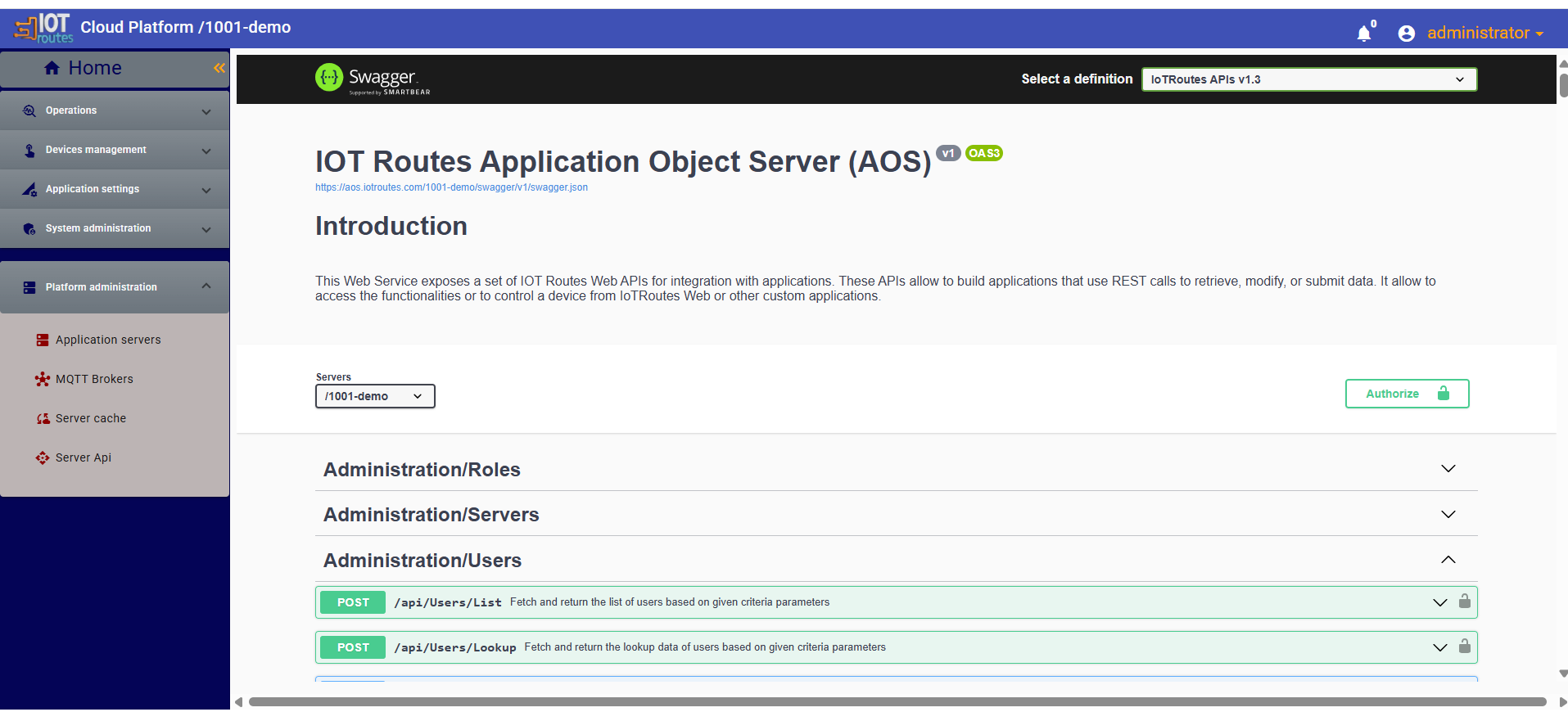
Full API documentation is available through Swagger at https://<your-AOS-url>/swagger/index.html.
API documentation is also accessible from the web client under Platform Administration → Server API, where an embedded Swagger UI allows users to test API calls directly.
When this embedded Swagger is opened, the platform automatically retrieves the current user’s bearer token; the user can simply paste it into the Authorize dialog to authenticate Swagger requests, making it possible to execute API calls with the permissions of the currently logged-in user.
2. Authentication
IoTRoutes uses Bearer tokens (JWT) for authentication and authorization for all APIs, and also Client ID /API key for APIs acced by devices. JWT Tokens are issued when a user logs in via the platform or through the /api/auth endpoint.
Login request example:
Successful response:
The token must then be included in the Authorization header of every subsequent API call: Authorization: Bearer <tokenid>
3. API Conventions
| Element | Description |
|---|---|
| Format | JSON request and response payloads. |
| Naming | Resource-oriented URLs (e.g., /devices,/attributes , /messages). |
| Pagination | Supported via page, size , filter and sort queryOptions parameter. |
| Timestamps | ISO 8601 format (UTC). |
| Errors | Returned with standard HTTP codes and JSON error details. |
Example error response
Best Practices
Use tokens securely — never expose them in client-side code or logs.
Use pagination for all list endpoints to optimize performance.
Leverage filters (status, class, dateFrom, dateTo) for analytics queries.
Combine APIs and Workflows — trigger or extend workflows directly from external systems using HTTP requests.
Monitor API limits — large installations may enforce rate limits per user or token.
Test on sandbox — use a test environment before deploying integrations to production.